Wat zap java
Author: d | 2025-04-24

Permainan Java wat zap web - Muat turun dengan Nokia, Samsung, Motorola, LG, Sony Ericsson, Blackberry dan untuk semua telefon bimbit J2ME yang disokong Java yang lain. Jogos Java de wat zap web - Fa a o download com Nokia, Samsung, Motorola, LG, Sony Ericsson, Blackberry e para todos os outros celulares J2ME compat veis com Java.
PHONEKY - Permainan Java wat zap web
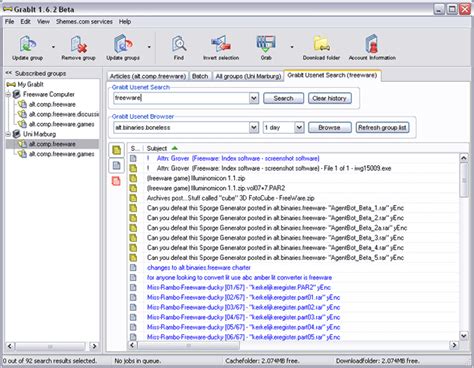
In the ever-evolving landscape of cybersecurity, protecting web applications from potential threats is a top priority. The Open Web Application Security Project (OWASP) plays a crucial role in this endeavor, offering a range of tools and resources. One standout tool is OWASP Zed Attack Proxy (ZAP), a feature-rich and open-source security testing tool designed for web applications. In this article, we will embark on a journey to unravel the world of OWASP ZAP, exploring its features, applications, and providing a beginner-friendly guide to using this powerful tool.What is OWASP ZAP?OWASP ZAP is a penetration testing tool for finding vulnerabilities in web applications. It stands as an OWASP flagship project, contributing significantly to the organization’s mission of improving the security of software. ZAP is specifically designed for both automated and manual testing of web applications’ security, making it a versatile tool for developers, security professionals, and ethical hackers.Why Use OWASP ZAP?1. Comprehensive Security Testing:ZAP provides a wide range of features for testing web applications, including automated scanners, various tools for manual testing, and support for various attack modes.2. Vulnerability Detection:ZAP helps identify vulnerabilities such as cross-site scripting (XSS), SQL injection, security misconfigurations, and more. Detecting and addressing these issues is crucial for securing web applications.3. Ease of Use:ZAP’s user-friendly interface makes it accessible for both beginners and experienced security professionals. The tool provides guidance and recommendations throughout the testing process.4. Automation Capabilities:ZAP supports automated scanning, allowing users to set up and execute tests quickly. This is particularly useful for regular security assessments and integration into continuous integration/continuous deployment (CI/CD) pipelines.5. Active and Passive Scanning:ZAP offers both active and passive scanning modes. Active scanning involves actively sending requests to the application to identify vulnerabilities, while passive scanning observes and analyzes the traffic for potential issues.Basic OWASP ZAP Usage:1. Installation:Before diving into OWASP ZAP, you need to have it installed on your system. ZAP is a Java-based application and is available for Windows, Linux, and macOS. You can download the latest version from the official OWASP ZAP website.2. Launching OWASP ZAP:Once installed, you can launch ZAP. The tool has a graphical user interface (GUI) accessible through your web browser. You can also run it in headless mode for automation.3. Setting Up Target:Before conducting any tests, you need to set up a target, which is the web application you want to test. Enter the target URL in the “Quick Start” tab of the ZAP interface and click “Attack.”4. Spidering:ZAP’s spidering functionality helps map out the structure of the target application by following links. This can be initiated by clicking the “Spider” tab and configuring the spider settings.5. Active Scanning:ZAP’s active scanning feature identifies security vulnerabilities by sending malicious payloads to the target application. You can initiate an active scan by clicking the “Active Scan” tab and selecting the target.6. Passive Scanning:Passive scanning occurs automatically as ZAP intercepts and analyzes HTTP traffic. This helps identify potential security issues without actively sending payloads to the application.7. Reviewing Results:After scanning is complete, navigate to the “Alerts” tab Permainan Java wat zap web - Muat turun dengan Nokia, Samsung, Motorola, LG, Sony Ericsson, Blackberry dan untuk semua telefon bimbit J2ME yang disokong Java yang lain. Finding and exploiting web application vulnerabilities. It is easy to use and extend and features dozens of web assessment and exploitation plugins.New Features:-> Considerably increased performance by implementing gzip encoding-> Enhanced embedded bug report system using Trac’s XMLRPC-> Fixed hundreds of bugs * Fixed critical bug in auto-update feature-> Enhanced integration with other tools (bug fixed and added more info to the file)Download W3af OWASP Zed Attack Proxy (ZAP)The OWASP Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications.It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing as well as being a useful addition to an experienced pen testers toolbox.Some of ZAP ‘s features:Intercepting ProxyAutomated scannerPassive scannerBrute Force scannerSpiderFuzzerPort scannerDynamic SSL certificatesAPIBeanshell integrationDownload ZAPWebSploit FrameworkWebSploit Is An Open Source Project For Scan And Analysis Remote System From Vulnerability.Description:[+]Autopwn – Used From Metasploit For Scan and Exploit Target Service[+]wmap – Scan,Crawler Target Used From Metasploit wmap plugin[+]format infector – inject reverse & bind payload into file format[+]phpmyadmin – Search Target phpmyadmin login page[+]lfi – Scan,Bypass local file inclusion Vulnerability & can be bypass some WAF[+]apache users – search server username directory (if use from apache webserver)[+]Dir Bruter – brute target directory with wordlist[+]admin finder – search admin & login page of target[+]MLITM Attack – Man Left In The Middle, XSS Phishing Attacks[+]MITM – Man In The Middle Attack[+]Java Applet Attack – Java Signed Applet Attack[+]MFOD Attack Vector – Middle Finger Of Doom Attack Vector[+]USB Infection Attack – Create Executable Backdoor For Infect USB For WindowsDownloadUniscan Vulnerability ScannerThe Uniscan vulnerability scanner is aimed at information security, which aims at finding vulnerabilities in Web systems and is licensed under the GNU GENERAL PUBLIC LICENSE 3.0 (GPL 3). The Uniscan was developed using the Perl programming language to be easier to work with text, has an easy to use regular expressions and is also multi-threaded.Uniscan FeaturesIdentification of system pages through a Web Crawler.Use of threads in the crawler.Control the maximum number of requests the crawler.Control of variation of system pages identified by Web Crawler.Control of file extensions that are ignored.Test of pages found via the GET method.Test the forms found via the POST method.Support for SSL requests (HTTPS).Proxy support.Official Change Log :– Uniscan is now Modularized.– Added directory checks.– Added file checks.– Added PUT method enabled check.– Bug fix in crawler when found ../ directory.– Crawler support POST method.– Configuration by file uniscan.conf.– Added checks for backup of files found by crawler.– Added Blind SQL-i checks.– Added static RCE, RFI, LFI checks.– Crawler improved by checking /robots.txt.– improved XSS vulnerability detection.– improvedComments
In the ever-evolving landscape of cybersecurity, protecting web applications from potential threats is a top priority. The Open Web Application Security Project (OWASP) plays a crucial role in this endeavor, offering a range of tools and resources. One standout tool is OWASP Zed Attack Proxy (ZAP), a feature-rich and open-source security testing tool designed for web applications. In this article, we will embark on a journey to unravel the world of OWASP ZAP, exploring its features, applications, and providing a beginner-friendly guide to using this powerful tool.What is OWASP ZAP?OWASP ZAP is a penetration testing tool for finding vulnerabilities in web applications. It stands as an OWASP flagship project, contributing significantly to the organization’s mission of improving the security of software. ZAP is specifically designed for both automated and manual testing of web applications’ security, making it a versatile tool for developers, security professionals, and ethical hackers.Why Use OWASP ZAP?1. Comprehensive Security Testing:ZAP provides a wide range of features for testing web applications, including automated scanners, various tools for manual testing, and support for various attack modes.2. Vulnerability Detection:ZAP helps identify vulnerabilities such as cross-site scripting (XSS), SQL injection, security misconfigurations, and more. Detecting and addressing these issues is crucial for securing web applications.3. Ease of Use:ZAP’s user-friendly interface makes it accessible for both beginners and experienced security professionals. The tool provides guidance and recommendations throughout the testing process.4. Automation Capabilities:ZAP supports automated scanning, allowing users to set up and execute tests quickly. This is particularly useful for regular security assessments and integration into continuous integration/continuous deployment (CI/CD) pipelines.5. Active and Passive Scanning:ZAP offers both active and passive scanning modes. Active scanning involves actively sending requests to the application to identify vulnerabilities, while passive scanning observes and analyzes the traffic for potential issues.Basic OWASP ZAP Usage:1. Installation:Before diving into OWASP ZAP, you need to have it installed on your system. ZAP is a Java-based application and is available for Windows, Linux, and macOS. You can download the latest version from the official OWASP ZAP website.2. Launching OWASP ZAP:Once installed, you can launch ZAP. The tool has a graphical user interface (GUI) accessible through your web browser. You can also run it in headless mode for automation.3. Setting Up Target:Before conducting any tests, you need to set up a target, which is the web application you want to test. Enter the target URL in the “Quick Start” tab of the ZAP interface and click “Attack.”4. Spidering:ZAP’s spidering functionality helps map out the structure of the target application by following links. This can be initiated by clicking the “Spider” tab and configuring the spider settings.5. Active Scanning:ZAP’s active scanning feature identifies security vulnerabilities by sending malicious payloads to the target application. You can initiate an active scan by clicking the “Active Scan” tab and selecting the target.6. Passive Scanning:Passive scanning occurs automatically as ZAP intercepts and analyzes HTTP traffic. This helps identify potential security issues without actively sending payloads to the application.7. Reviewing Results:After scanning is complete, navigate to the “Alerts” tab
2025-04-02Finding and exploiting web application vulnerabilities. It is easy to use and extend and features dozens of web assessment and exploitation plugins.New Features:-> Considerably increased performance by implementing gzip encoding-> Enhanced embedded bug report system using Trac’s XMLRPC-> Fixed hundreds of bugs * Fixed critical bug in auto-update feature-> Enhanced integration with other tools (bug fixed and added more info to the file)Download W3af OWASP Zed Attack Proxy (ZAP)The OWASP Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications.It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing as well as being a useful addition to an experienced pen testers toolbox.Some of ZAP ‘s features:Intercepting ProxyAutomated scannerPassive scannerBrute Force scannerSpiderFuzzerPort scannerDynamic SSL certificatesAPIBeanshell integrationDownload ZAPWebSploit FrameworkWebSploit Is An Open Source Project For Scan And Analysis Remote System From Vulnerability.Description:[+]Autopwn – Used From Metasploit For Scan and Exploit Target Service[+]wmap – Scan,Crawler Target Used From Metasploit wmap plugin[+]format infector – inject reverse & bind payload into file format[+]phpmyadmin – Search Target phpmyadmin login page[+]lfi – Scan,Bypass local file inclusion Vulnerability & can be bypass some WAF[+]apache users – search server username directory (if use from apache webserver)[+]Dir Bruter – brute target directory with wordlist[+]admin finder – search admin & login page of target[+]MLITM Attack – Man Left In The Middle, XSS Phishing Attacks[+]MITM – Man In The Middle Attack[+]Java Applet Attack – Java Signed Applet Attack[+]MFOD Attack Vector – Middle Finger Of Doom Attack Vector[+]USB Infection Attack – Create Executable Backdoor For Infect USB For WindowsDownloadUniscan Vulnerability ScannerThe Uniscan vulnerability scanner is aimed at information security, which aims at finding vulnerabilities in Web systems and is licensed under the GNU GENERAL PUBLIC LICENSE 3.0 (GPL 3). The Uniscan was developed using the Perl programming language to be easier to work with text, has an easy to use regular expressions and is also multi-threaded.Uniscan FeaturesIdentification of system pages through a Web Crawler.Use of threads in the crawler.Control the maximum number of requests the crawler.Control of variation of system pages identified by Web Crawler.Control of file extensions that are ignored.Test of pages found via the GET method.Test the forms found via the POST method.Support for SSL requests (HTTPS).Proxy support.Official Change Log :– Uniscan is now Modularized.– Added directory checks.– Added file checks.– Added PUT method enabled check.– Bug fix in crawler when found ../ directory.– Crawler support POST method.– Configuration by file uniscan.conf.– Added checks for backup of files found by crawler.– Added Blind SQL-i checks.– Added static RCE, RFI, LFI checks.– Crawler improved by checking /robots.txt.– improved XSS vulnerability detection.– improved
2025-04-17License: All | Free This software tool allows you to control your WAT-1000 1/3 camera from your personal computer. This software tool allows you to control your Wat-1000 1/3 camera from your personal computer. The camera has the following specifications: -Wide Dynamic Range 120dB -High resolution 520TVL -Smear free -Multi functions -RS-232 -Day&Night function -On screen display -White balance mode -Flickerless mode -AGC/MGC... Category: Multimedia & Design / VideoPublisher: Watec inc, License: Freeware, Price: USD $0.00, File Size: 953.0 KBPlatform: Windows Ancient Roman Colosseum, England Stonehenge, and Angkor Wat in Cambodia, such as the Great Wall, the world would sleep in a huge mystery and excitement just heard the name of the chest. The album "Ancient World" that appeared to look more powerful and contents than "2", dating back to age seven wonders of the world seek further. Construction of the seven wonders where help match while playing the 3. Collected the maps available at each level, it'll show up at the location of the eighth. Kimi is really all you can conquer the land. Category: Utilities / Command Line UtilitiesPublisher: Pachinko, License: Freeware, Price: USD $0.00, File Size: 0Platform: Windows, Mac, Linux, Pocket PC, Other, Android, BlackBerry, iPhone, iPod, iTouch, Palm, Not Applicable, Unix, Handheld/Mobile Other, Java, MS-DOS, AS/400 Creates a nice HTML-page from your IE bookmarks/favorites. Creates a nice HTML-page from your IE bookmarks/favorites. Put your bookmarks into maps and you'll have a startpage-look-a-like HTML-page. You can modify: title, discription, keywords, language, advertisment-links. What you'll see is Wat you get. The program is in English and Dutch. Several pages on the internet are created with this program. For example Category: Internet / Misc. PluginsPublisher: ABC-EDUCA, License: Freeware, Price: USD $0.00, File Size: 1.5 MBPlatform: Windows Remove pieces like in a normal checkers game. Remove pieces like in a normal checkers game. Move diagonally jumping over a piece into an empty square removing a piece in this process. Only one piece may be removed in one move. It is fairly easy to Remove 30 to 39 pieces. It is challenging to Remove 40 to 44 and a substantial achievement to Remove 45 to 47. Category: Games / Misc. GamesPublisher: Ihsan Ul Haque, License: Freeware, Price: USD $0.00, File Size: 296.6 KBPlatform: Windows Remove Clock does just what it says. Remove Clock does just what it says...it removes your clock from your Windows taskbar. And puts it back as well. This simple program is able tohide your tray clock for you. Category: Desktop EnhancementsPublisher: appsapps.info, License: Freeware, Price: USD $0.00, File Size: 143.0 KBPlatform: Windows Toolbar Cleaner is a utility that will remove any toolbar and toolbar-related files from your system. Toolbar Cleaner is a utility that will Remove any
2025-04-08Beschrijving Informatie Alle versies Reviews Bandicam is hoge kwaliteit software voor het opnemen van spellen, video's en alles wat er op uw computerscherm gebeurd.U kunt met Bandicam opnames maken van o.a.: Minecraft, WOW, MapleStory, iTunes, YouTube, PowerPoint, Excel, Firefox, HDTV, Webcamera, Skype, Video chatten, Java/Flash spellen, Streaming video en uw desktop scherm.FunktiesDirectX/OpenGL Opname (*.avi)Rechthoekig Scherm Opname (*.avi)Afbeelding Opname (BMP, PNG, JPG)H.264, Xvid, MPEG-1, MJPEG, MP2, PCM ondersteuningFPS Controlle/OverlayVoordelenCreëer opmerkelijk kleinere videobestanden met super kwaliteit.Meer dan 24 uur video opnemen in 1 opname en bestand.Video's opnemen met een resolutie tot aan 2560x1600Upload je video naar Youtube zonder te converteren (720p/1080p)De maximum bestandsgrootte is ongelimiteerd (meer dan 3.9GB) HTML code om naar deze pagina te linken: Trefwoorden: bandicam screenshot opnemen vastleggen beeldscherm Licentietype Shareware1 Datum waarop toegevoegd 6 mei 2015 Downloads 65 Bestandsgrootte 9.06 MB ( Besturingssystemen Vista / Win2k / Win7 / Win8 / WinXP1 1De licentie en de besturingssysteem informatie is gebaseerd op de laatste versie van de software. Nog geen beoordelingen van gebruikers
2025-04-22To review the identified vulnerabilities. ZAP categorizes issues by severity, providing insights into potential risks.Practical Examples:1. Spidering the Target:Open ZAP and enter the target URL in the “Quick Start” tab.Click “Attack” to initiate the spidering process.Navigate to the “Spider” tab to view the progress and results.2. Active Scanning:After spidering, click the “Active Scan” tab.Select the target and configure scan settings.Click “Start Scan” to initiate the active scanning process.3. Reviewing Alerts:Once scanning is complete, go to the “Alerts” tab.Review the categorized list of vulnerabilities and click on each to see detailed information.Tips for Beginners:1. Explore the Interface:Spend time exploring the ZAP interface to familiarize yourself with its various tabs and features. Understanding the layout will enhance your efficiency in using the tool.2. Follow the ZAP User Guide:The OWASP ZAP User Guide provides comprehensive documentation. Refer to it for detailed information on each feature and best practices for using ZAP effectively.3. Customize Your Tests:ZAP allows you to customize your tests by adjusting scanning policies, configuring spidering options, and setting various parameters. Experiment with these settings to tailor ZAP to your specific needs.4. Join the Community:OWASP has an active community, and ZAP has its own dedicated community forums. Engage with the community to ask questions, share experiences, and learn from others.Conclusion:OWASP ZAP stands as a pivotal tool in the arsenal of web security professionals, offering a user-friendly yet powerful solution for identifying vulnerabilities in web applications. For beginners, delving into ZAP may seem like entering a complex realm, but with patience and exploration, it becomes a valuable asset in the pursuit of securing digital assets. Whether you are a developer aiming to enhance the security of your applications or a cybersecurity enthusiast keen on ethical hacking, OWASP ZAP provides the tools needed to identify and address potential risks. So, install ZAP, set your target, and embark on a journey to fortify the security of web applications in the ever-evolving landscape of cybersecurity.DockerHub LinkTo try out a demo environment for different vulnerabilities, you can visit our DockerHub repository here TutorialVideo tutorials for exploiting vulnerabilities are available here
2025-04-14IPTV Zap Player on PCIPTV Zap Player, coming from the developer Zap IPTV Studio, is running on Android systerm in the past.Now, You can play IPTV Zap Player on PC with GameLoop smoothly.Download it in the GameLoop library or search results. No more eyeing the battery or frustrating calls at the wrong time any more.Just enjoy IPTV Zap Player PC on the large screen for free!IPTV Zap Player IntroductionZap IPTV Player is a mobile and Android TV video streaming application that comes with the following features, among others:- Friendly and easy-to-use user interface- Supports high audio/video quality and media control with an integrated VLC player- Supports using external VLC or MX players for playing content- Details for Movies/Series from IMDB (genre, cast, plot, etc)- 20 supported languages- Customization of categories - show/hide content categories (if present in the provided content)- Favorites category - store all your favorite content in one place, for easy accessIMPORTANT NOTE:- We are not offering any kind of IPTV services like IPTV subscriptions, or streams.- The user has to contact the TV Service Provider for Username, Password, Server URL, or Playlist (M3u file / URL)- The user must have their own content, this is just an IPTV app that provides the platform to play the content.DISCLAIMER:- ZAP IPTV PLAYER APP does not supply or include any media or content. Users must provide their own content for streaming.- ZAP IPTV PLAYER APP has no affiliation with any third-party provider whatsoever.- ZAP IPTV PLAYER APP does not endorse the streaming of copyright-protected material without the copyright holder’s permission.
2025-03-26